Vitalik Buterin by way of the Vitalik Buterin Weblog
This can be a mirror of the put up at https://medium.com/@VitalikButerin/zk-snarks-under-the-hood-b33151a013f6
That is the third a part of a collection of articles explaining how the expertise behind zk-SNARKs works; the earlier articles on quadratic arithmetic packages and elliptic curve pairings are required studying, and this text will assume data of each ideas. Primary data of what zk-SNARKs are and what they do can be assumed. See additionally Christian Reitwiessner’s article right here for one more technical introduction.
Within the earlier articles, we launched the quadratic arithmetic program, a means of representing any computational downside with a polynomial equation that’s far more amenable to numerous types of mathematical trickery. We additionally launched elliptic curve pairings, which permit a really restricted type of one-way homomorphic encryption that allows you to do equality checking. Now, we’re going to begin from the place we left off, and use elliptic curve pairings, along with a number of different mathematical methods, with the intention to enable a prover to show that they know an answer for a selected QAP with out revealing the rest concerning the precise resolution.
This text will give attention to the Pinocchio protocol by Parno, Gentry, Howell and Raykova from 2013 (usually referred to as PGHR13); there are a number of variations on the fundamental mechanism, so a zk-SNARK scheme carried out in follow may go barely otherwise, however the primary ideas will usually stay the identical.
To begin off, allow us to go into the important thing cryptographic assumption underlying the safety of the mechanism that we’re going to use: the *knowledge-of-exponent* assumption.
Principally, when you get a pair of factors � and �, the place �⋅�=�, and also you get a degree �, then it’s not potential to provide you with �⋅� until � is “derived” from � indirectly that you already know. This will likely appear intuitively apparent, however this assumption truly can’t be derived from some other assumption (eg. discrete log hardness) that we often use when proving safety of elliptic curve-based protocols, and so zk-SNARKs do in reality relaxation on a considerably shakier basis than elliptic curve cryptography extra typically — though it’s nonetheless sturdy sufficient that the majority cryptographers are okay with it.
Now, let’s go into how this can be utilized. Supposed {that a} pair of factors (�,�) falls from the sky, the place �⋅�=�, however no one is aware of what the worth of � is. Now, suppose that I provide you with a pair of factors (�,�) the place �⋅�=�. Then, the KoE assumption implies that the one means I may have made that pair of factors was by taking � and �, and multiplying each by some issue r that I personally know. Be aware additionally that because of the magic of elliptic curve pairings, checking that �=�⋅� doesn’t truly require figuring out � – as a substitute, you may merely verify whether or not or not �(�,�)=�(�,�).
Let’s do one thing extra attention-grabbing. Suppose that we have now ten pairs of factors fall from the sky: (�1,�1),(�2,�2)…(�10,�10). In all instances, ��⋅�=��. Suppose that I then give you a pair of factors (�,�) the place �⋅�=�. What are you aware now? You understand that � is a few linear mixture �1⋅�1+�2⋅�2+…+�10⋅�10, the place I do know the coefficients �1,�2…�10. That’s, the one strategy to arrive at such a pair of factors (�,�) is to take some multiples of �1,�2…�10 and add them collectively, and make the identical calculation with �1,�2…�10.
Be aware that, given any particular set of �1…�10 factors that you simply would possibly need to verify linear combos for, you may’t truly create the accompanying �1…�10 factors with out figuring out what � is, and when you do know what � is then you may create a pair (�,�) the place �⋅�=� for no matter � you need, with out bothering to create a linear mixture. Therefore, for this to work it’s completely crucial that whoever creates these factors is reliable and really deletes � as soon as they created the ten factors. That is the place the idea of a “trusted setup” comes from.
Do not forget that the answer to a QAP is a set of polynomials (�,�,�) such that �(�)⋅�(�)−�(�)=�(�)⋅�(�), the place:
- � is a linear mixture of a set of polynomials {�1…��}
- � is the linear mixture of {�1…��} with the identical coefficients
- � is a linear mixture of {�1…��} with the identical coefficients
The units {�1…��},{�1…��} and {�1…��} and the polynomial � are a part of the issue assertion.
Nonetheless, in most real-world instances, �,� and � are extraordinarily giant; for one thing with many 1000’s of circuit gates like a hash perform, the polynomials (and the elements for the linear combos) might have many 1000’s of phrases. Therefore, as a substitute of getting the prover present the linear combos instantly, we’re going to use the trick that we launched above to have the prover show that they’re offering one thing which is a linear mixture, however with out revealing the rest.
You may need observed that the trick above works on elliptic curve factors, not polynomials. Therefore, what truly occurs is that we add the next values to the trusted setup:
- �⋅�1(�),�⋅�1(�)⋅��
- �⋅�2(�),�⋅�2(�)⋅��
- …
- �⋅�1(�),�⋅�1(�)⋅��
- �⋅�2(�),�⋅�2(�)⋅��
- …
- �⋅�1(�),�⋅�1(�)⋅��
- �⋅�2(�),�⋅�2(�)⋅��
- …
You may consider t as a “secret level” at which the polynomial is evaluated. � is a “generator” (some random elliptic curve level that’s specified as a part of the protocol) and �,��,�� and �� are “poisonous waste”, numbers that completely should be deleted in any respect prices, or else whoever has them will have the ability to make faux proofs. Now, if somebody provides you a pair of factors �, � such that �⋅��=� (reminder: we don’t want �� to verify this, as we will do a pairing verify), then you already know that what they’re supplying you with is a linear mixture of �� polynomials evaluated at �.
Therefore, thus far the prover should give:
- ��=�⋅�(�),��′=�⋅�(�)⋅��
- ��=�⋅�(�),��′=�⋅�(�)⋅��
- ��=�⋅�(�),��′=�⋅�(�)⋅��
Be aware that the prover doesn’t truly have to know (and shouldn’t know!) �,��,�� or �� to compute these values; moderately, the prover ought to have the ability to compute these values simply from the factors that we’re including to the trusted setup.
The subsequent step is to be sure that all three linear combos have the identical coefficients. This we will do by including one other set of values to the trusted setup: �⋅(��(�)+��(�)+��(�))⋅�, the place � is one other quantity that ought to be thought of “poisonous waste” and discarded as quickly because the trusted setup is accomplished. We are able to then have the prover create a linear mixture with these values with the identical coefficients, and use the identical pairing trick as above to confirm that this worth matches up with the offered �+�+�.
Lastly, we have to show that �⋅�−�=�⋅�. We do that as soon as once more with a pairing verify:
�(��,��)/�(��,�)?=�(�ℎ,�⋅�(�))
The place �ℎ=�⋅�(�). If the connection between this equation and �⋅�−�=�⋅� doesn’t make sense to you, return and browse the article on pairings.
We noticed above the way to convert �,� and � into elliptic curve factors; � is simply the generator (ie. the elliptic curve level equal of the primary). We are able to add �⋅�(�) to the trusted setup. � is more durable; � is only a polynomial, and we predict little or no forward of time about what its coefficients shall be for every particular person QAP resolution. Therefore, we have to add but extra information to the trusted setup; particularly the sequence:
�,�⋅�,�⋅�2,�⋅�3,�⋅�4….
Within the Zcash trusted setup, the sequence right here goes as much as about 2 million; that is what number of powers of � you might want to just be sure you will all the time have the ability to compute �(�), at the very least for the precise QAP occasion that they care about. And with that, the prover can present all the data for the verifier to make the ultimate verify.
There’s yet one more element that we have to talk about. More often than not we don’t simply need to show within the summary that some resolution exists for some particular downside; moderately, we need to show both the correctness of some particular resolution (eg. proving that when you take the phrase “cow” and SHA3 hash it 1,000,000 instances, the ultimate outcome begins with 0x73064fe5), or {that a} resolution exists when you limit a number of the parameters. For instance, in a cryptocurrency instantiation the place transaction quantities and account balances are encrypted, you need to show that you already know some decryption key ok such that:
decrypt(old_balance, ok) >= decrypt(tx_value, ok)decrypt(old_balance, ok) - decrypt(tx_value, ok) = decrypt(new_balance, ok)
The encrypted old_balance, tx_value and new_balance ought to be specified publicly, as these are the precise values that we wish to confirm at that exact time; solely the decryption key ought to be hidden. Some slight modifications to the protocol are wanted to create a “customized verification key” that corresponds to some particular restriction on the inputs.
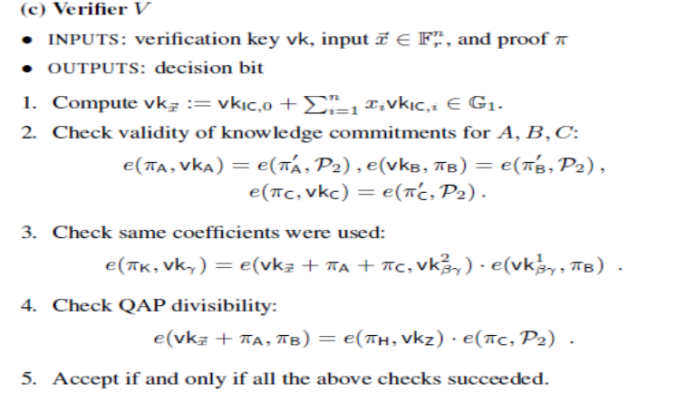
Now, let’s step again a bit. To start with, right here’s the verification algorithm in its entirety, courtesy of ben Sasson, Tromer, Virza and Chiesa:

The primary line offers with parametrization; primarily, you may consider its perform as being to create a “customized verification key” for the precise occasion of the issue the place a number of the arguments are specified. The second line is the linear mixture verify for �,� and �; the third line is the verify that the linear combos have the identical coefficients, and the fourth line is the product verify �⋅�−�=�⋅�.
Altogether, the verification course of is a number of elliptic curve multiplications (one for every “public” enter variable), and 5 pairing checks, one in every of which incorporates a further pairing multiplication. The proof incorporates eight elliptic curve factors: a pair of factors every for �(�),�(�) and �(�), a degree �� for �⋅(�(�)+�(�)+�(�)), and a degree �ℎ for �(�). Seven of those factors are on the �� curve (32 bytes every, as you may compress the � coordinate to a single bit), and within the Zcash implementation one level (��) is on the twisted curve in ��2 (64 bytes), so the overall measurement of the proof is ~288 bytes.
The 2 computationally hardest components of making a proof are:
- Dividing (�⋅�−�)/� to get � (algorithms based mostly on the Quick Fourier remodel can do that in sub-quadratic time, but it surely’s nonetheless fairly computationally intensive)
- Making the elliptic curve multiplications and additions to create the �(�),�(�),�(�) and �(�) values and their corresponding pairs
The fundamental motive why making a proof is so exhausting is the truth that what was a single binary logic gate within the authentic computation turns into an operation that should be cryptographically processed via elliptic curve operations if we’re making a zero-knowledge proof out of it. This truth, along with the superlinearity of quick Fourier transforms, implies that proof creation takes ~20–40 seconds for a Zcash transaction.
One other essential query is: can we attempt to make the trusted setup a bit of… much less trust-demanding? Sadly we will’t make it fully trustless; the KoE assumption itself precludes making unbiased pairs (��,��⋅�) with out figuring out what � is. Nonetheless, we will improve safety enormously by utilizing �-of-� multiparty computation – that’s, developing the trusted setup between � events in such a means that so long as at the very least one of many members deleted their poisonous waste then you definately’re okay.
To get a little bit of a really feel for the way you’ll do that, right here’s a easy algorithm for taking an present set (�,�⋅�,�⋅�2,�⋅�3…), and “including in” your individual secret so that you simply want each your secret and the earlier secret (or earlier set of secrets and techniques) to cheat.
The output set is just:
�,(�⋅�)⋅�,(�⋅�2)⋅�2,(�⋅�3)⋅�3…
Be aware you could produce this set figuring out solely the unique set and s, and the brand new set capabilities in the identical means because the previous set, besides now utilizing �⋅� because the “poisonous waste” as a substitute of �. So long as you and the particular person (or folks) who created the earlier set don’t each fail to delete your poisonous waste and later collude, the set is “secure”.
Doing this for the whole trusted setup is kind of a bit more durable, as there are a number of values concerned, and the algorithm must be achieved between the events in a number of rounds. It’s an space of energetic analysis to see if the multi-party computation algorithm could be simplified additional and made to require fewer rounds or made extra parallelizable, because the extra you are able to do that the extra events it turns into possible to incorporate into the trusted setup process. It’s cheap to see why a trusted setup between six members who all know and work with one another would possibly make some folks uncomfortable, however a trusted setup with 1000’s of members can be almost indistinguishable from no belief in any respect – and when you’re actually paranoid, you will get in and take part within the setup process your self, and make sure that you personally deleted your worth.
One other space of energetic analysis is using different approaches that don’t use pairings and the identical trusted setup paradigm to attain the identical purpose; see Eli ben Sasson’s latest presentation for one different (although be warned, it’s at the very least as mathematically difficult as SNARKs are!)
Particular because of Ariel Gabizon and Christian Reitwiessner for reviewing.
- web optimization Powered Content material & PR Distribution. Get Amplified As we speak.
- PlatoData.Community Vertical Generative Ai. Empower Your self. Entry Right here.
- PlatoAiStream. Web3 Intelligence. Data Amplified. Entry Right here.
- PlatoESG. Carbon, CleanTech, Power, Setting, Photo voltaic, Waste Administration. Entry Right here.
- PlatoHealth. Biotech and Scientific Trials Intelligence. Entry Right here.
- BlockOffsets. Modernizing Environmental Offset Possession. Entry Right here.
- Supply: Plato Information Intelligence.